As our world becomes increasingly digital, cybersecurity has emerged as one of the most critical issues of our time. From online banking to remote work, smart homes, and cloud storage, almost every aspect of daily life depends on technology. While this creates opportunities for growth and convenience, it also introduces significant risks. Cybercriminals are constantly developing new strategies, and 2025 is shaping up to be a defining year for how individuals and businesses defend themselves online.
This article explores the state of cybersecurity in 2025, the most common threats, strategies to stay safe, the role of governments and businesses, and future trends shaping the digital security landscape.
1. Why Cybersecurity Matters in 2025
Cybersecurity is no longer just an IT concern—it is a matter of personal safety, financial stability, and national security. Data breaches, ransomware attacks, and identity theft have become common headlines, costing billions of dollars each year. With more devices connected to the Internet of Things (IoT), the attack surface for hackers is larger than ever.
Protecting data, systems, and networks is essential not only for businesses but also for individuals. Without robust cybersecurity, sensitive information such as medical records, financial accounts, and personal communications are at risk of exposure or misuse.
2. The Biggest Cybersecurity Threats in 2025
2.1 Ransomware Attacks – Ransomware remains one of the most destructive threats. Hackers encrypt data and demand payment for its release. Businesses, hospitals, and government agencies are common targets because of the critical nature of their data.
2.2 Phishing and Social Engineering – Cybercriminals exploit human psychology to trick individuals into sharing sensitive information. Advanced phishing emails and deepfake voice/video scams make it harder than ever to spot fraudulent attempts.
2.3 IoT Vulnerabilities – From smart fridges to connected cars, IoT devices often lack strong security protections. Hackers can exploit these weak points to access entire networks.
2.4 Cloud Security Risks – As businesses migrate to the cloud, misconfigured systems and poor access controls open the door to unauthorized access and data leaks.
2.5 AI-Powered Cyberattacks – Artificial intelligence is not just used for defense—it is also being leveraged by hackers to launch more sophisticated and automated attacks.
2.6 Insider Threats – Not all threats come from outside. Disgruntled employees or careless staff can unintentionally expose organizations to risk by mishandling data or credentials.
3. Strategies for Individuals to Stay Safe
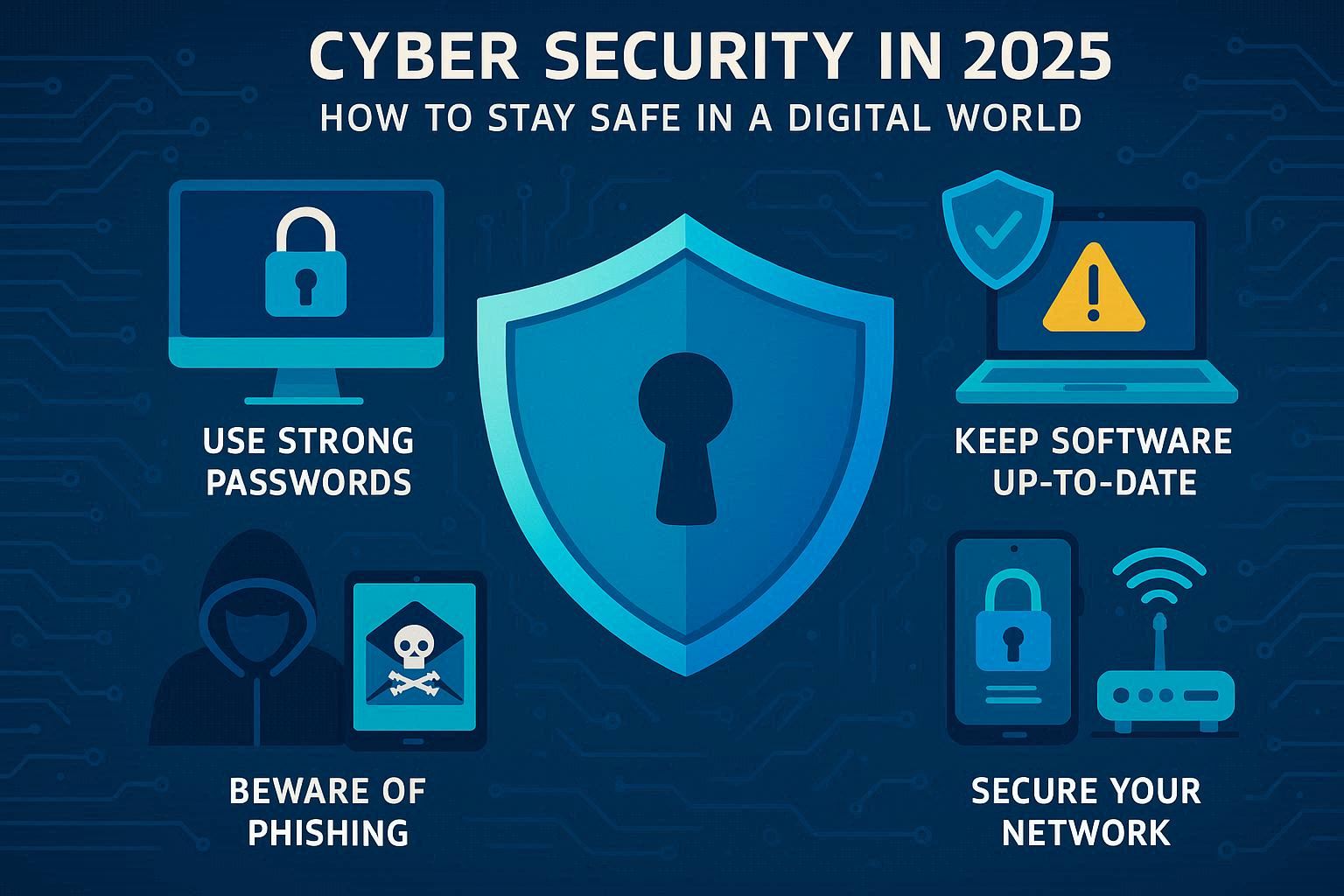
3.1 Use Strong, Unique Passwords – Weak or reused passwords remain a common vulnerability. Using a password manager can help generate and store secure credentials for all accounts.
3.2 Enable Multi-Factor Authentication (MFA) – MFA adds an extra layer of security by requiring more than just a password. Even if a hacker steals login credentials, access is blocked without the second verification step.
3.3 Keep Software Updated – Outdated software often contains known vulnerabilities. Regularly updating devices and applications ensures patches are applied to fix security flaws.
3.4 Be Cautious with Links and Attachments – Avoid clicking on suspicious links or downloading attachments from unknown sources, as they may contain malware.
3.5 Secure Home Networks – Changing default router passwords, using strong Wi-Fi encryption, and updating IoT devices help protect home environments from cyber intrusions.
3.6 Regular Backups – Maintaining backups of critical files ensures that even in the event of ransomware, data can be restored without paying criminals.
4. Cybersecurity for Businesses
4.1 Employee Training – Employees are often the weakest link in security. Regular training helps them recognize phishing attempts and follow best practices.
4.2 Zero Trust Architecture – Instead of assuming trust within a network, Zero Trust requires continuous verification of all users and devices, reducing the chance of breaches.
4.3 Endpoint Security – With remote work now common, securing laptops, smartphones, and other devices is critical. Businesses must deploy advanced endpoint protection tools.
4.4 Incident Response Plans – Companies should prepare for potential attacks with clear incident response procedures, ensuring quick recovery and minimal damage.
4.5 Data Encryption – Encrypting sensitive information ensures that even if data is stolen, it remains unreadable without the proper decryption keys.
4.6 Third-Party Risk Management – Businesses often rely on vendors and partners. Assessing their cybersecurity practices prevents supply chain attacks.
5. The Role of Governments and Global Cooperation
Cybersecurity is a global issue that requires cooperation beyond borders. Governments are increasingly passing laws to protect citizens’ data and strengthen critical infrastructure. In 2025, initiatives such as mandatory cybersecurity compliance for businesses, international treaties on cybercrime, and investment in public awareness campaigns are becoming more common.
Global cooperation is essential because cybercriminals operate across jurisdictions. Joint task forces, intelligence sharing, and international agreements are helping nations combat cyber threats more effectively.
6. The Future of Cybersecurity
Looking ahead, several trends will define cybersecurity in the coming years:
6.1 Artificial Intelligence for Defense – AI is being deployed to detect suspicious patterns, automate threat responses, and predict vulnerabilities before they are exploited.
6.2 Quantum Computing Challenges – Quantum computers have the potential to break traditional encryption. As this technology develops, cybersecurity experts are working on quantum-resistant algorithms.
6.3 Biometric Authentication – Fingerprint, facial recognition, and even behavioral biometrics are being adopted as safer alternatives to passwords.
6.4 Greater Regulation – Governments are expected to enforce stricter cybersecurity rules, especially for critical sectors like finance, healthcare, and energy.
6.5 Cybersecurity as a Service – Small and medium businesses are turning to third-party providers for affordable, scalable cybersecurity solutions.
Conclusion
Cybersecurity in 2025 is no longer optional—it is essential. With threats ranging from ransomware to AI-powered attacks, individuals and businesses must remain vigilant. By adopting best practices such as strong authentication, regular updates, encryption, and employee training, risks can be significantly reduced.
Governments, businesses, and individuals must work together to create a safer digital environment. The future of cybersecurity lies in innovation, global cooperation, and continuous education. Staying proactive is the key to thriving in an increasingly digital world.